Digital Forensics Evidences
- Computer Forensics Evidence
- Mobile Forensics Evidence
- Network Forensics Evidence
- Cloud Forensics Evidence
- Database Forensics Evidence
- Multimedia Forensics Evidence
In the digital age, forensic science has expanded beyond traditional realms, entering the intricate world of digital forensics. This discipline is pivotal in modern investigations, dealing with the recovery and analysis of digital evidences. As technology evolves, the types of digital forensics evidences diversify, each playing a crucial role in solving crimes and understanding cyber incidents.
Understanding Digital Forensics
Digital forensics is a branch of forensic science focusing on evidence found in digital devices and cyber environments. It has grown from addressing simple computer crimes to encompassing a broad range of devices and data types. The evolution of digital forensics mirrors the rapid advancement of technology, highlighting its increasing importance in law enforcement, legal contexts, and corporate settings.
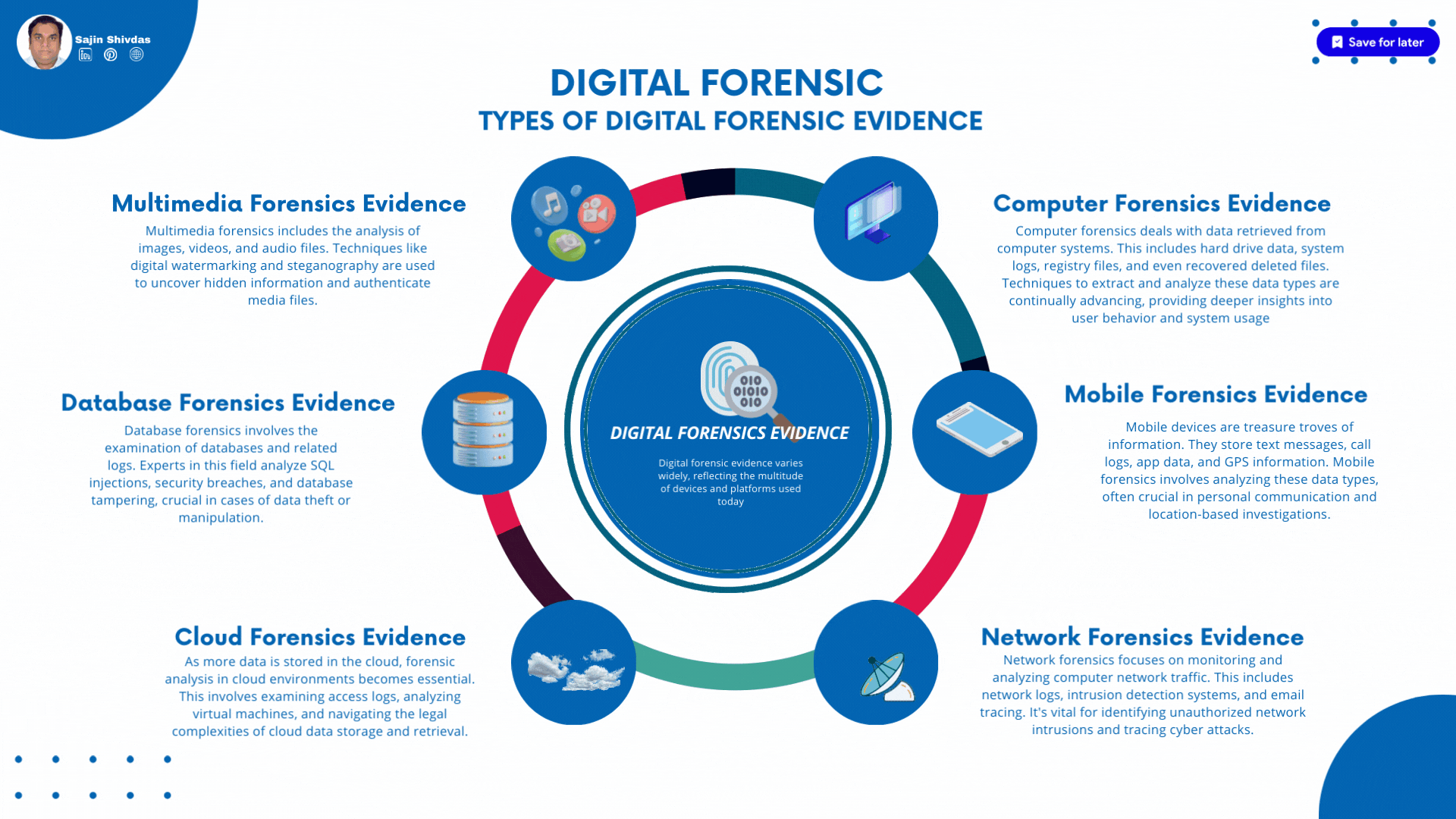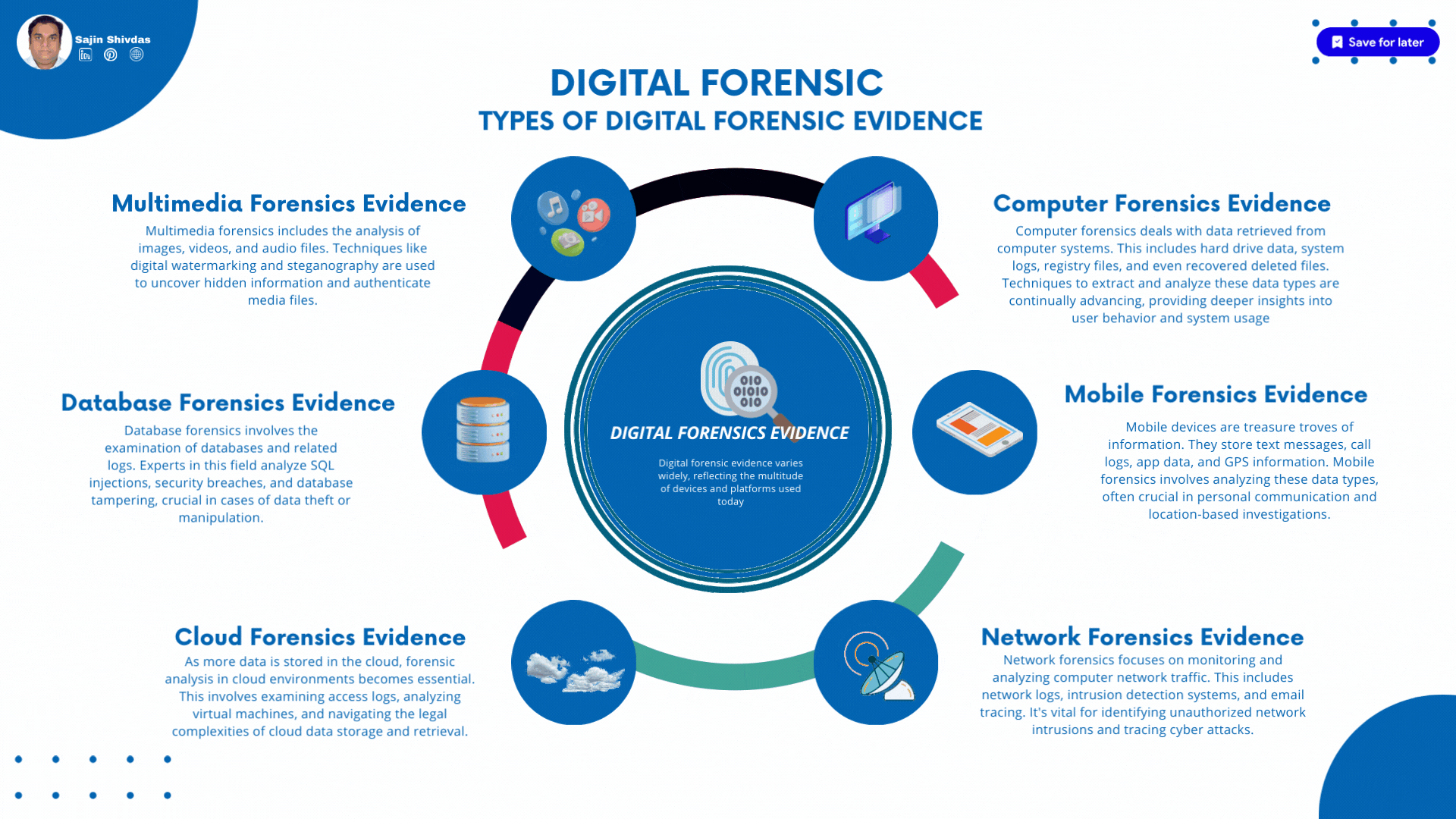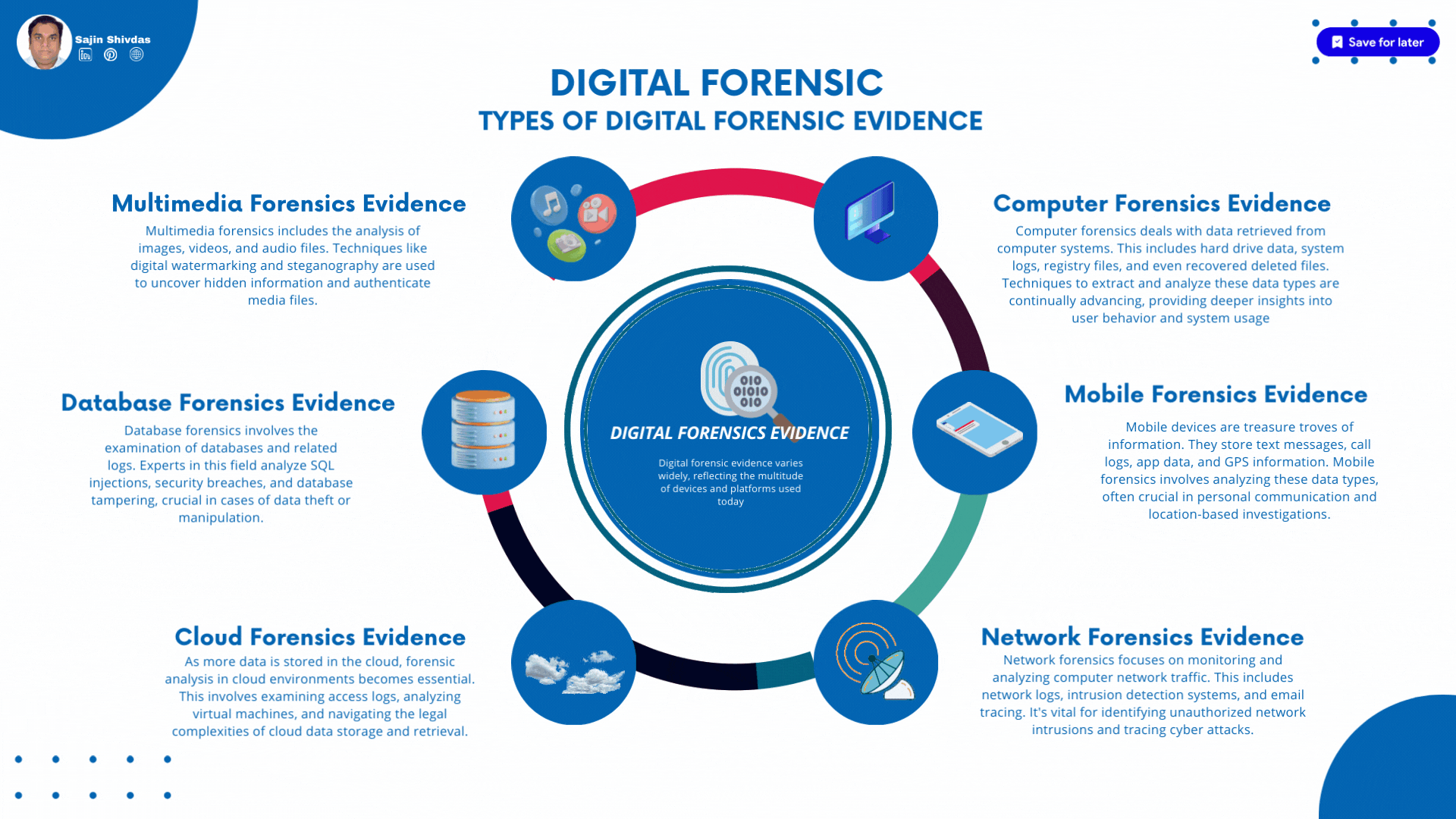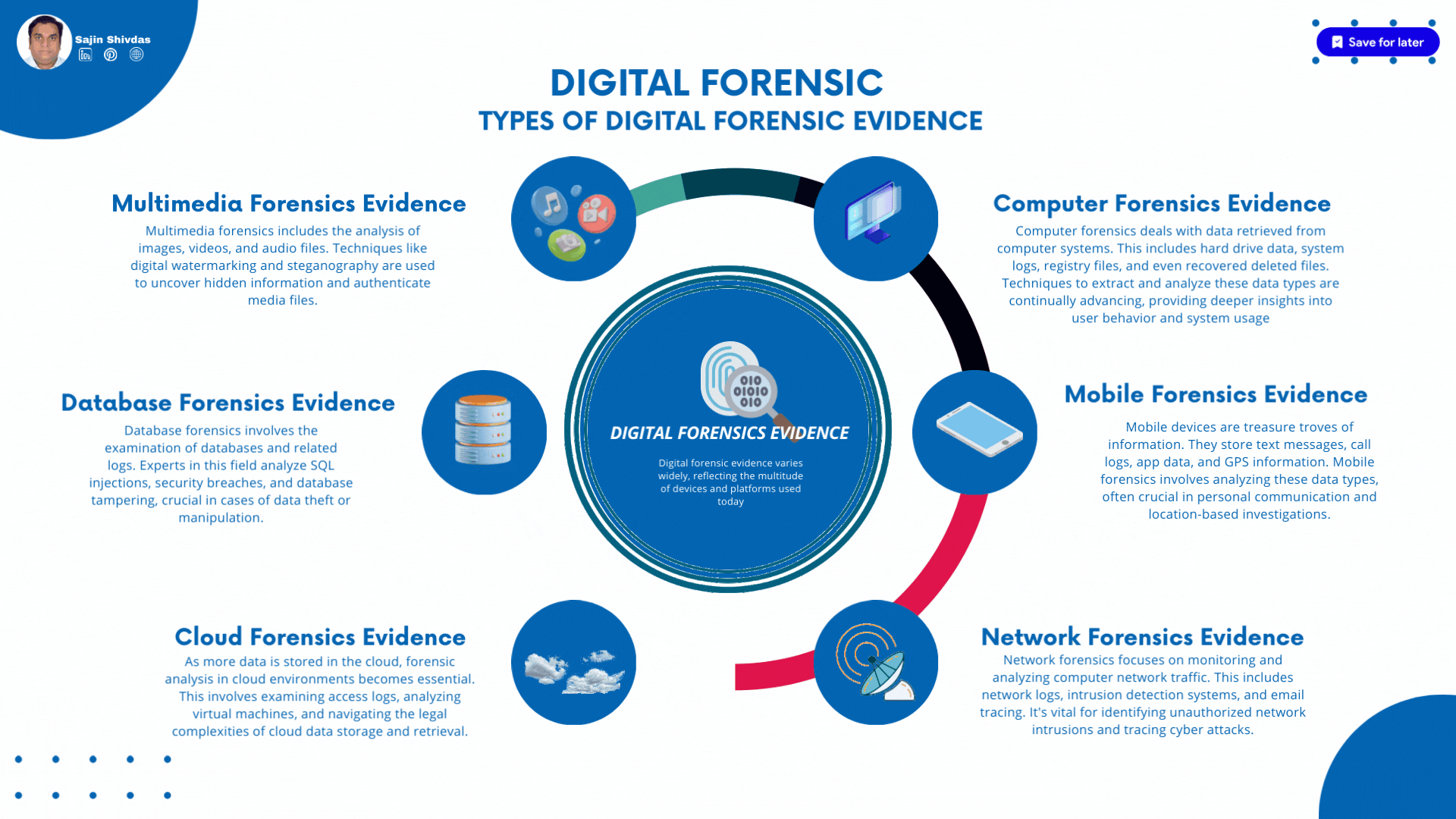
Types of Digital Forensic Evidence
Digital forensic evidence varies widely, reflecting the multitude of devices and platforms used today. This evidence can be categorized into several types:
Computer Forensics Evidence
Computer forensics deals with data retrieved from computer systems. This includes hard drive data, system logs, registry files, and even recovered deleted files. Techniques to extract and analyze these data types are continually advancing, providing deeper insights into user behavior and system usage.
Mobile Forensics Evidence
Mobile devices are treasure troves of information. They store text messages, call logs, app data, and GPS information. Mobile forensics involves analyzing these data types, often crucial in personal communication and location-based investigations.
Network Forensics Evidence
Network forensics focuses on monitoring and analyzing computer network traffic. This includes network logs, intrusion detection systems, and email tracing. It’s vital for identifying unauthorized network intrusions and tracing cyber attacks.
Cloud Forensics Evidence
As more data is stored in the cloud, forensic analysis in cloud environments becomes essential. This involves examining access logs, analyzing virtual machines, and navigating the legal complexities of cloud data storage and retrieval.
Database Forensics Evidence
Database forensics involves the examination of databases and related logs. Experts in this field analyze SQL injections, security breaches, and database tampering, crucial in cases of data theft or manipulation.
Multimedia Forensics Evidence
Multimedia forensics includes the analysis of images, videos, and audio files. Techniques like digital watermarking and steganography are used to uncover hidden information and authenticate media files.









