Mobile Forensics Process
Mobile digital forensics is a branch of digital forensics that focuses on the recovery and investigation of data found in mobile devices, including smartphones, tablets, and other portable electronic devices. This field has become increasingly important due to the widespread use of mobile devices and their capacity to store a vast amount of personal and sensitive information, such as contacts, messages, emails, images, videos, location data, and app data.
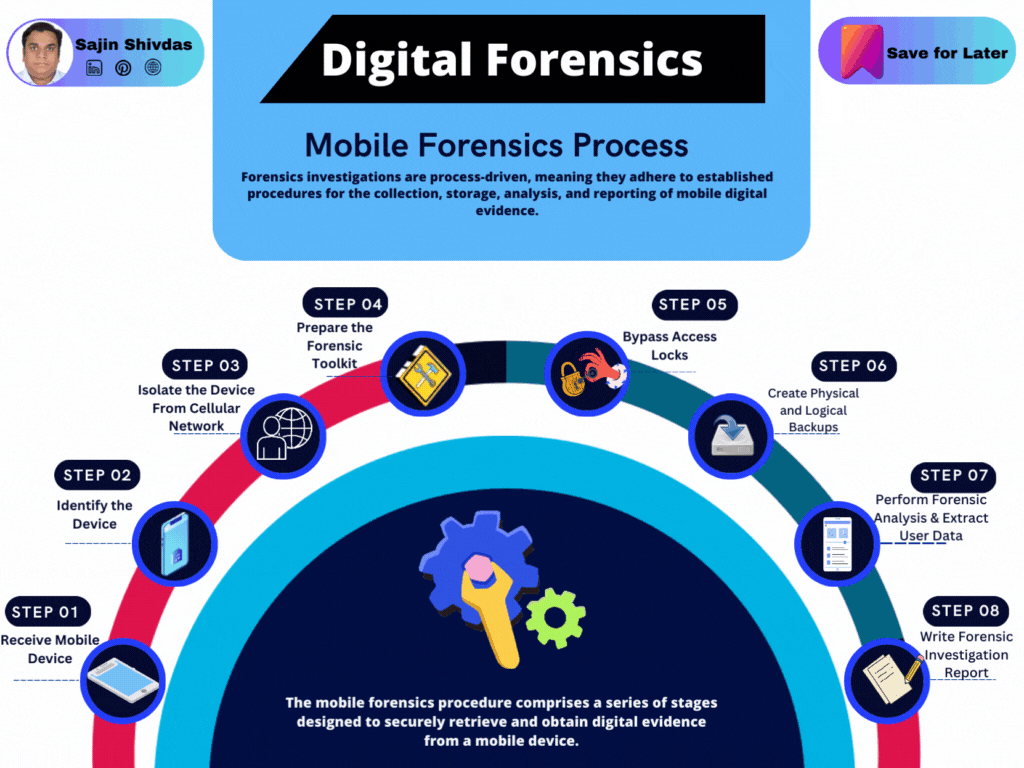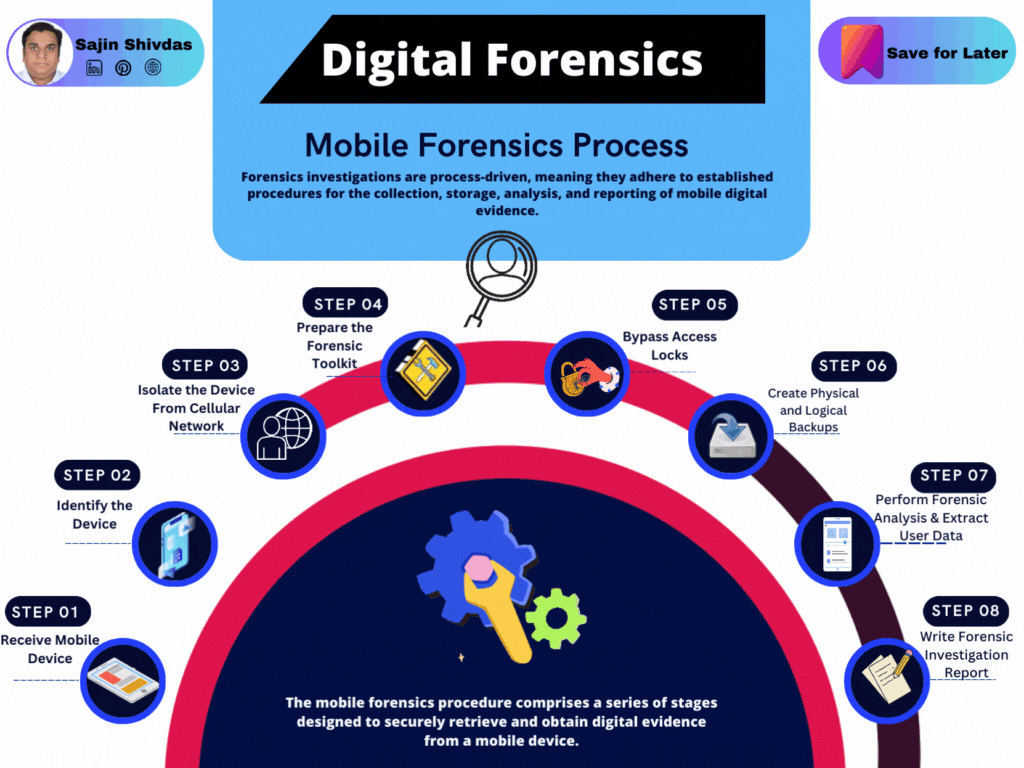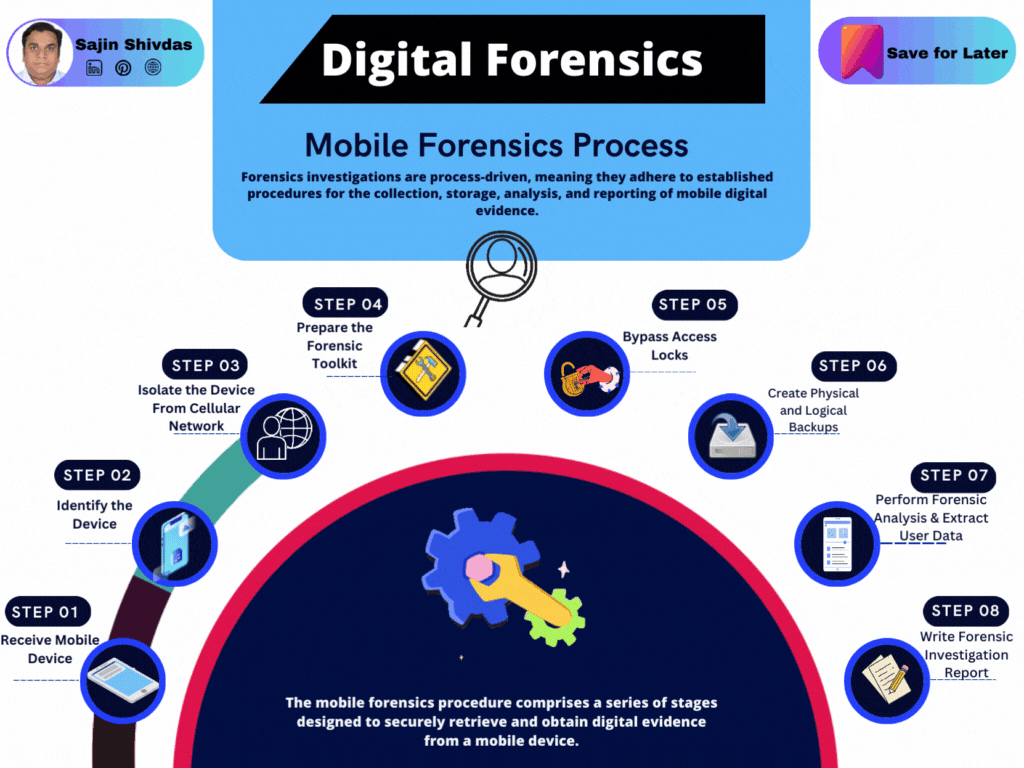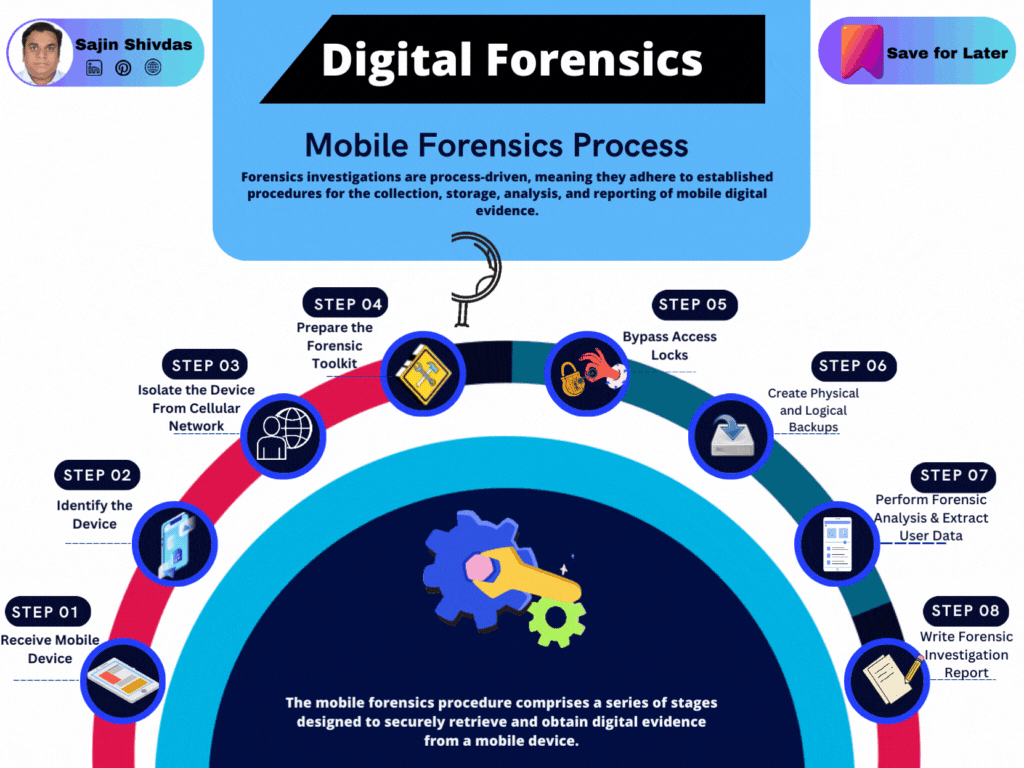
Identify the Device
Identifying the device involves determining the make, model, operating system version, and any other relevant specifications. This information is crucial for selecting the appropriate tools and methods for forensic extraction and analysis. Understanding the device’s specifics helps in planning the acquisition strategy, as different devices and operating systems may have unique security features or data storage structures.
Isolate the Device From Cellular Network
Isolating the device from any networks (cellular, Wi-Fi, Bluetooth) is critical to prevent incoming or outgoing communications that could alter the data on the device. This is typically achieved using a Faraday bag or box, which blocks electromagnetic fields, or by activating the device’s airplane mode, followed by ensuring all connectivity options are disabled. This step ensures the data remains in its original state, preventing remote wipes, updates, or notifications that could compromise the evidence.
Prepare the Forensic Toolkit
Preparing the forensic toolkit involves selecting and readying the tools and software needed for the forensic acquisition and analysis. This includes physical connectors and cables, write blockers to prevent data from being altered during the analysis, and specialized software tools designed for mobile forensics. The selection of tools depends on the device’s make and model and the type of data extraction planned (physical, logical, or file system extraction).
Bypass Access Locks
Bypassing access locks is often necessary to access the data on a device. This can be one of the most challenging aspects of mobile forensics due to the increasing security features of modern devices. Techniques can include exploiting vulnerabilities, using manufacturer codes, or leveraging forensic software tools that can bypass or unlock devices. The legality and ethical implications of bypassing locks must be carefully considered, with appropriate legal authority.
Create Physical and Logical Backups
Creating both physical and logical backups ensures that all potentially relevant data is preserved. A physical backup involves creating a bit-for-bit copy of the entire device, including deleted spaces, which might contain recoverable deleted data. A logical backup includes files and settings accessible through the device’s operating system. These backups ensure that the original data remains unchanged, and analysts can return to the raw data if needed during the investigation.
Perform Forensic Analysis & Extract User Data
Forensic analysis involves using various tools and techniques to examine the backups and extract relevant user data. This can include call logs, messages, emails, images, videos, app data, and location information. The analysis aims to reconstruct events, uncover deleted data, and identify patterns of use that are relevant to the investigation. Tools can provide timeline analysis, keyword searches, and data carving capabilities to assist in this process.
Write Forensic Investigation Report
The final step is writing a detailed forensic investigation report that documents the entire process, including the methods used for acquisition and analysis, the findings, and any conclusions drawn from the data. The report should be clear, concise, and understandable to individuals without technical expertise. It must include all relevant information to support legal proceedings, including an executive summary, detailed findings, and an appendix with technical details and evidence documentation.









