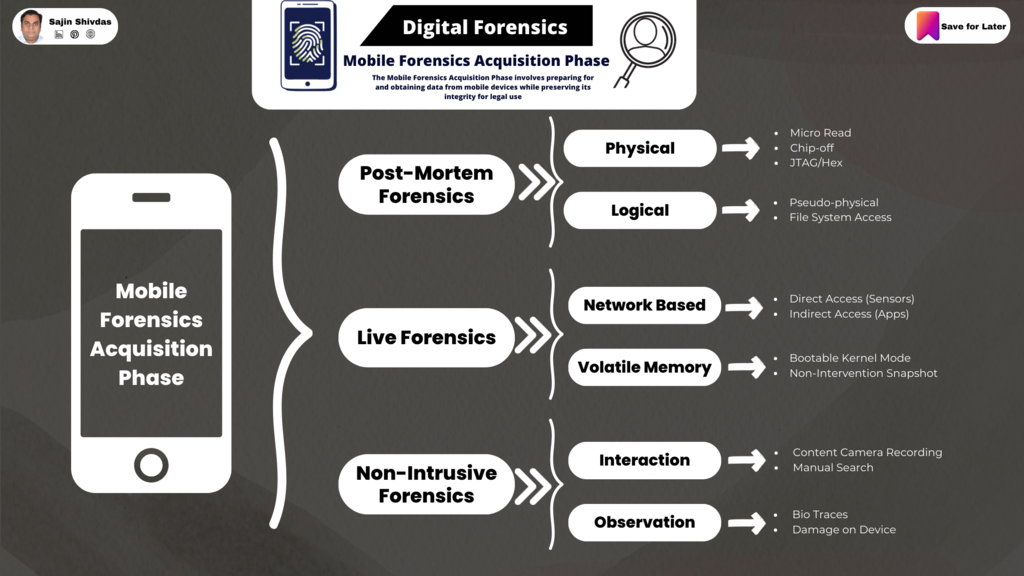
Mobile Forensics - Acquisition Phase
Diving into the Acquisition Phase of forensics, we’re looking at a meticulous process divided into three main areas: Post-Mortem Forensics, Live Forensics, and Non-Intrusive Forensics.
Post-Mortem Forensics
- Physical
- Micro Read
- Chip-off
- JTAG/Hex
- Logical
- Pseudo-physical
- File System Access
Live Forensics
-
Network Based
- Direct Access (Sensors)
- Indirect Access (Apps)
-
-
Volatile Memory
- Bootable Kernel Mode
- Non-Intervention Snapshot
-
Non-intrusive Forensics
- Interaction
- Content Camera Recording
- Manual Search
- Observation
- Bio Traces
- Damage on Device
Mobile Forensics Acquisition Phase
Post-Mortem Forensics
Physical
Micro Read
Zooming in to read data directly from microchips with specialized equipment.
Chip-off
Physically removing a chip from the device to extract data. It’s pretty much digital surgery.
JTAG/Hex
Using the JTAG or Hex interface to get a raw image of the data, bypassing standard security.
Logical
Pseudo-physical
A deep dive that’s not quite physical but gets us close to that level of access.
File System Access
Straight-up accessing the file system, looking at the files and folders directly.
Network Based
Direct Access (Sensors)
Getting data straight from network sensors.
Indirect Access (Apps)
Using applications to indirectly gather data from the network.
Volatile Memory
Bootable Kernel Mode
Booting the device in a special mode to access memory.
Non-Intervention Snapshot
Taking a snapshot of the memory without messing with the system.
Live Forensics
Non-Intrusive Forensics
Interaction
Content Camera Recording
Recording what’s happening on the device screen.
Manual Search
Physically searching the device without software tools.
Observation
Bio Traces
Looking for biological evidence (like fingerprints).
Damage on Device
Checking for physical damage that could tell a story.









