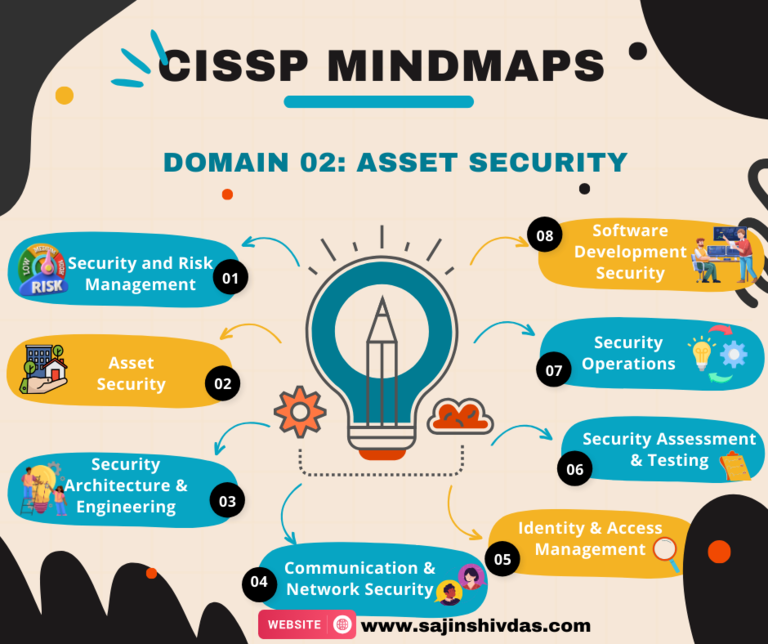
CISSP Mindmap – Domain 02: Asset Security
A comprehensive CISSP Mindmap Series will include all 8 Domains. This collection is designed to equip prospective CISSP professionals with essential resources for exam preparation, training and reference.
CISSP Mindmap - Domain 02
CISSP Interactive Mindmap
Domain_02: Key Concepts and Terminology
- Asset Inventory: Maintaining a detailed inventory of all information assets, including hardware, software, data, and personnel.
- Asset Ownership: Identifying and assigning owners for each asset, who are responsible for ensuring appropriate protection.
- Asset Classification: Categorizing assets based on their value, sensitivity, and impact on the organization if compromised (e.g., public, confidential, secret).
- Data States: Recognizing the three states of data: at rest, in transit, and in use.
- Data Retention: Policies governing how long data should be retained and when it should be securely disposed of.
- Data Masking and Obfuscation: Techniques to obscure data, reducing exposure of sensitive information while maintaining its utility.
Understanding the data life cycle phases
- Create: Data creation or acquisition.
- Store: Safe storage of data, ensuring integrity and confidentiality.
- Use: Proper access control and handling during usage.
- Share: Controlled sharing or distribution.
- Archive: Long-term retention for reference or compliance.
- Destroy: Secure disposal when no longer needed.
- Classification Levels: Categorizing data based on its sensitivity (e.g., public, internal, confidential, highly confidential).
- Labeling: Applying appropriate labels indicating the classification of data.
- Encryption: Protecting data in transit and at rest using cryptographic methods.
- Access Control: Mechanisms to enforce who can access data, such as role-based access control (RBAC).
- Data Leakage Prevention (DLP): Tools and policies to prevent unauthorized data transfer or exposure.
- Media Sanitization: Techniques for securely erasing data from storage media.
- Media Storage: Policies for the secure handling and storage of media containing sensitive data.
- Personally Identifiable Information (PII): Understanding regulations and protections for PII.
- Data Masking: Techniques used to protect PII or sensitive data by replacing it with functional, but not real, data.
- Policies governing the handling, storage, and destruction of information based on its classification.
- Understanding the impact of legal jurisdictions on data storage and handling.
- Least Privilege: Ensuring users and systems have the minimum access required to perform their functions.
- Data Owner: The entity responsible for data management, classification, and protection.
- Data Custodian: The individual or team responsible for the safe custody, transport, and implementation of security policies for data.
- Sanitization: Methods like clearing, purging, and destroying data to ensure it cannot be recovered.
- Asset Management
-
- Asset Inventory: Maintaining a detailed inventory of all information assets, including hardware, software, data, and personnel.
- Asset Ownership: Identifying and assigning owners for each asset, who are responsible for ensuring appropriate protection.
- Asset Classification: Categorizing assets based on their value, sensitivity, and impact on the organization if compromised (e.g., public, confidential, secret).
- Data Security
-
- Data States: Recognizing the three states of data: at rest, in transit, and in use.
- Data Retention: Policies governing how long data should be retained and when it should be securely disposed of.
- Data Masking and Obfuscation: Techniques to obscure data, reducing exposure of sensitive information while maintaining its utility.
- Data Life Cycle
-
Understanding the data life cycle phases
- Create: Data creation or acquisition.
- Store: Safe storage of data, ensuring integrity and confidentiality.
- Use: Proper access control and handling during usage.
- Share: Controlled sharing or distribution.
- Archive: Long-term retention for reference or compliance.
- Destroy: Secure disposal when no longer needed.
- Data Classification
-
- Classification Levels: Categorizing data based on its sensitivity (e.g., public, internal, confidential, highly confidential).
- Labeling: Applying appropriate labels indicating the classification of data.
- Data Security Controls
-
- Encryption: Protecting data in transit and at rest using cryptographic methods.
- Access Control: Mechanisms to enforce who can access data, such as role-based access control (RBAC).
- Data Leakage Prevention (DLP): Tools and policies to prevent unauthorized data transfer or exposure.
- Media Management
-
- Media Sanitization: Techniques for securely erasing data from storage media.
- Media Storage: Policies for the secure handling and storage of media containing sensitive data.
- Data Privacy
-
- Personally Identifiable Information (PII): Understanding regulations and protections for PII.
- Data Masking: Techniques used to protect PII or sensitive data by replacing it with functional, but not real, data.
- Information Lifecycle Management
-
- Policies governing the handling, storage, and destruction of information based on its classification.
- Data Sovereignty
-
- Understanding the impact of legal jurisdictions on data storage and handling.
- Access Management
-
- Least Privilege: Ensuring users and systems have the minimum access required to perform their functions.
- Data Owner: The entity responsible for data management, classification, and protection.
- Data Custodian: The individual or team responsible for the safe custody, transport, and implementation of security policies for data.
- Data Disposal
-
- Sanitization: Methods like clearing, purging, and destroying data to ensure it cannot be recovered.
Domain_02: Key Terms & Definitions
- Asset Classification: Asset classification involves protecting them according to their value to the company. The owners of a company’s assets know their value best and should protect them.
- Classification: Classification arranges values in a hierarchical fashion. The most valuable classes to an organization are confidential, followed by proprietary, while the least valuable classes are public. Classes are selected by various organizations according to their requirements. Organizations utilize several classification schemes, therefore it’s not a good idea to commit any one to memory.
- Security Label: Security Labels are used to correlate security attributes with an information object’s data structure. Labels are read by the system to determine data classification and protection.
- Security Marking: Security marking is similar to security label, Method for assigning security properties to objects in a human-readable format. Labels are read to comprehend data classification and protection.
- Data Owner / Controller: The data owner, or data controller, is the most important role because they protect the data. The owner will define the categorization for data and the owner is then accountable for ensuring the data is safeguarded correctly.
- Data Custodian: Data custodians manage data technically. Custodians ensure data security, availability, capacity, backups, and restoration. They handle data technicalities.
- Crypto shredding: Crypto shredding involves encrypting data with an effective algorithm like AES 256 and destroying every duplicate of the encryption key. Crypto shredded and unrecoverable data is achieved by destroying the encryption key. Shredding crypto is between purging and clearing. The data cannot be recovered if the key is never recovered, brute forced, or the algorithm is not flawed. It was cleaned up. If any of those are true, the data may be recovered and was cleared.
- Digital Rights Management: Digital Rights Management (DRM) protects digital media copyright holders. DRM methods encrypt films, music files, eBooks, etc., allowing control over who may play them, how often, on what device, and whether they can be printed. Copyright holders can create and enforce usage rules with DRM technologies.
- Data Loss Prevention: Data Loss Prevention (DLP) solutions protect sensitive data against loss, abuse, and unauthorized access. Companies can identify, monitor, and secure data in use, motion, and rest using DLP systems. Data classification is essential for DLP systems. DLP systems can’t prevent all data from leaking or being exploited, thus organizations need data classification to identify sensitive data.
- Mantrap: Preventive 2-door physical control. Each door requires separate form of authentication
- Bollard: A post designed to stop a car, typically in front of building entrances
- Smart Card: Physical access control device with integrated circuit
- Tailgating: Following an authorized person into a building without providing credentials
- Object Rescue: The act of recovering information from previously used objects (files, tapes, etc.)
- Deleting: Removes the entry from the FAT and marks the blocks unallocated (data remains)
- Formatting: Destroys the FAT and creates new one (data remains)
- Overwriting: Writes over every character of a file or disk (more secure)
- Shredding/Wiping: Overwrites file data before removing the FAT entry
- Degaussing: Destroys the integrity of magnetic media through using a strong magnetic field
- Destruction: Physically damages the media itself (incinerating, pulverizing, acid bath, etc.)
Domain_02: Key Areas
- Information and Asset Classification
- Ownership and Control of Assets
- Privacy Protection
- Data Security Controls
- Handling and Retention Policies
- Physical Security
- Asset Management
- Information and Asset Ownership
Resources
- (ISC)2 CISSP Official Study Guide (OSG) 9th Edition by Mike Chapple, James Michael Stewart, and Darril Gibson
- Chapter 05, Pg179-218
- CISSP All-in-One Exam Guide, Ninth Editionby Fernando Maymi and Shon Harris
- Part II, Pg213-253
- Eleventh Hour CISSP® Study Guide, Third Editionby Eric Conrad, Seth Misenar, Joshua Feldma
- Domain-02, Pg33-46
- Destination Certification – A Concise Guideby Rob Witcher, John Berti, Lou Hablas, Nick Mitropoulos
- Domain-02, Pg71-96
-
The Official (ISC)2 CISSP CBK Reference, 6th Edition by Arthur Deane and Aaron Kraus
- Domain-02, Pg97-144
Books Reference
Practice Tests Reference
- (ISC)2 CISSP Official Practice Testsby Mike Chapple and David Seidl
- How to Think Like a Manager for the CISSP Examby Luke Ahmed
- Boson Practice Exam
- Study Notes and Theory (SNT) by Luke Ahmed
Videos Reference
- Mike Chapple’sCISSP Cert Prep on LinkedIn Learning.
- Kelly Handerhan’sCISSP Prep Course on Cybrary
- Destination CISSP Mindmap Video
- Pete Zerger’s CISSP Exam Cram
- Prabh’s Coffee Shots
- Luke Ahmed’s Study Notes and Theory (SNT)
Credits & Disclaimer
We express our gratitude to the below-mentioned authors, creators, and sources which have been referred for the creation of our Interactive CISSP Mindmap –Mike Chapple and David Seidl (OSG), Luke Ahmed (SNT), Pete Zerger (Exam Cram), Prashant Mohan (Memory Palace) , Prabh (Coffee shots), Rob Witcher (destcert.com/) and M. Waleed Khaliq (CISSP Concepts Guide).This Mindmap has been meticulously created to ensure that information is shared effectively. This Mindmap aims to offer a thorough grasp of essential concepts with a dedication to assist enhanced learning experiences. We hope that this resource helps people absorb information more thoroughly, which will lead to a broader understanding of each CISSP domains and is freely available for all.
Contribution
We have already included some reference images and short notes for most of the topics so that users can more effectively refer to the content in the mindmap. If you have any information, images, or notes that can make the mindmap more effective, please feel free to share them.
https://github.com/sajinshivdas/CISSP_Interactive_Mindmap/tree/main/CISSP_Domain_02
For issues and concern please feel free to raise a issue in Github link https://github.com/sajinshivdas/CISSP_Interactive_Mindmap/issues
Connect with me www.linkedin.com/in/sajin-shivdas
Related Mindmaps
Find the related mindmaps of CISSP Domains below.