CISSP Mindmap-Domain 8: Software Development Security
An Interactive CISSP Mindmap Series
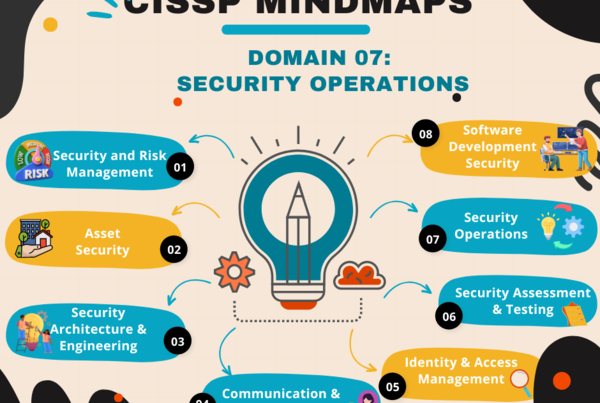
CISSP Mindmap – Domain 08
A comprehensive CISSP Mindmap Series will include all 8 Domains. This collection is designed to equip prospective CISSP professionals with essential resources for exam preparation, training and reference.
Domain_08: Key Concepts and Terminology
- SDLC Phases: Planning, Analysis, Design, Implementation, Testing, Deployment, and Maintenance.
- Secure Software Development: Incorporating security throughout the SDLC to ensure secure coding practices.
- Agile, Waterfall, Spiral: Common software development methodologies with varying approaches to development and project management.
- Object-Oriented Programming (OOP): Focuses on objects and data rather than actions and logic, using principles like inheritance, encapsulation, and polymorphism.
- Code Reuse: Utilizing pre-existing code for new applications to save development time and enhance reliability.
- API (Application Programming Interface): Allows software applications to communicate and share data/functionality.
- Secure Design Principles: Principles like least privilege, input validation, and error handling ensure the software is secure from the start.
- Threat Modelling: Identifying potential threats and designing mitigations to address security risks in software.
- Buffer Overflow: Occurs when data exceeds the buffer’s storage capacity, leading to potential system crashes or exploitation.
- SQL Injection: Attacks that allow an attacker to execute arbitrary SQL code on a database.
- Cross-Site Scripting (XSS): Injecting malicious scripts into web applications to exploit client-side vulnerabilities.
- Cross-Site Request Forgery (CSRF): Forces a user to execute unwanted actions on a web application they’re authenticated on.
- Input Validation: Ensuring all input is validated before processing to prevent injection attacks.
- Output Encoding: Encoding output to prevent injection vulnerabilities, such as XSS.
- Error Handling: Managing errors to avoid revealing system information to potential attackers.
- Static Analysis: Testing software without executing code (e.g., code reviews, static analysis tools).
- Dynamic Analysis: Testing software by executing code (e.g., fuzz testing, penetration testing).
- Fuzz Testing: Inputting random data into software to identify coding errors and security loopholes.
- Code Signing: Using digital signatures to verify the authenticity and integrity of software code.
- Obfuscation: Transforming code to make it difficult to understand or reverse-engineer, deterring attackers.
- Continuous Integration/Continuous Deployment (CI/CD): Automated testing and deployment of code to reduce vulnerabilities.
- DevSecOps: Integrating security practices into the DevOps process to ensure security is a priority throughout software development.
- Supply Chain Security: Ensuring the integrity and security of software acquired from third parties or open-source projects.
- Software Bill of Materials (SBOM): A list of components in a piece of software, helping to manage vulnerabilities in third-party components.
- SaaS (Software as a Service): Cloud-based software provided over the internet, with security managed by the service provider.
- IaaS/PaaS: Infrastructure and platform services provided in the cloud, where the user must manage security aspects within the deployed applications.
- OWASP (Open Web Application Security Project): Provides guidelines and tools for securing web applications.
- SANS Top 25: A list of the top 25 most dangerous software errors to avoid during development.
- Software Development Life Cycle (SDLC)
-
- SDLC Phases: Planning, Analysis, Design, Implementation, Testing, Deployment, and Maintenance.
- Secure Software Development: Incorporating security throughout the SDLC to ensure secure coding practices.
- Agile, Waterfall, Spiral: Common software development methodologies with varying approaches to development and project management.
- Programming Concepts
-
- Object-Oriented Programming (OOP): Focuses on objects and data rather than actions and logic, using principles like inheritance, encapsulation, and polymorphism.
- Code Reuse: Utilizing pre-existing code for new applications to save development time and enhance reliability.
- API (Application Programming Interface): Allows software applications to communicate and share data/functionality.
- Security in Software Design
-
- Secure Design Principles: Principles like least privilege, input validation, and error handling ensure the software is secure from the start.
- Threat Modelling: Identifying potential threats and designing mitigations to address security risks in software.
- Common Security Issues
-
- Buffer Overflow: Occurs when data exceeds the buffer’s storage capacity, leading to potential system crashes or exploitation.
- SQL Injection: Attacks that allow an attacker to execute arbitrary SQL code on a database.
- Cross-Site Scripting (XSS): Injecting malicious scripts into web applications to exploit client-side vulnerabilities.
- Cross-Site Request Forgery (CSRF): Forces a user to execute unwanted actions on a web application they’re authenticated on.
- Secure Coding Practices
-
- Input Validation: Ensuring all input is validated before processing to prevent injection attacks.
- Output Encoding: Encoding output to prevent injection vulnerabilities, such as XSS.
- Error Handling: Managing errors to avoid revealing system information to potential attackers.
- Software Testing
-
- Static Analysis: Testing software without executing code (e.g., code reviews, static analysis tools).
- Dynamic Analysis: Testing software by executing code (e.g., fuzz testing, penetration testing).
- Fuzz Testing: Inputting random data into software to identify coding errors and security loopholes.
- Code and Application Security
-
- Code Signing: Using digital signatures to verify the authenticity and integrity of software code.
- Obfuscation: Transforming code to make it difficult to understand or reverse-engineer, deterring attackers.
- Security in Deployment
-
- Continuous Integration/Continuous Deployment (CI/CD): Automated testing and deployment of code to reduce vulnerabilities.
- DevSecOps: Integrating security practices into the DevOps process to ensure security is a priority throughout software development.
- Acquired and Third-Party Software
-
- Supply Chain Security: Ensuring the integrity and security of software acquired from third parties or open-source projects.
- Software Bill of Materials (SBOM): A list of components in a piece of software, helping to manage vulnerabilities in third-party components.
- Cloud and Managed Services
-
- SaaS (Software as a Service): Cloud-based software provided over the internet, with security managed by the service provider.
- IaaS/PaaS: Infrastructure and platform services provided in the cloud, where the user must manage security aspects within the deployed applications.
- Software Development Frameworks
-
- OWASP (Open Web Application Security Project): Provides guidelines and tools for securing web applications.
- SANS Top 25: A list of the top 25 most dangerous software errors to avoid during development.
Domain_08: Key Terms & Definitions
Secure Software Development Life Cycle (Secure SDLC): A process that incorporates security considerations and practices throughout the software development lifecycle, from initial design to deployment and maintenance, to ensure the software is secure by design.
Application Security (AppSec): Practices and tools used to protect applications from threats and vulnerabilities at all stages of the development process, including design, development, deployment, and maintenance.
Static Application Security Testing (SAST): A testing methodology that analyzes source code, byte code, or binary code for security vulnerabilities without executing the program.
Dynamic Application Security Testing (DAST): A testing methodology that examines an application during its runtime to identify security vulnerabilities by simulating attacks.
Software Composition Analysis (SCA): A process that identifies and evaluates the security, licensing, and quality of open-source and third-party components within an application.
Threat Modeling: A proactive approach to identify, assess, and mitigate potential security threats to a software application at an early stage in the development process.
Secure Coding Practices: Guidelines and best practices for writing software code that is resistant to vulnerabilities and exploits, including input validation, proper error handling, and adherence to principle of least privilege.
Encryption: The process of converting data into a coded format to prevent unauthorized access, commonly used for data at rest and data in transit within applications.
Identity and Access Management (IAM): Frameworks and technologies used to ensure that only authorized individuals can access certain resources, and that they can do so only in a manner approved by the organization.
Penetration Testing: The practice of simulating cyber-attacks on a computer system, network, or web application to identify security weaknesses that could be exploited by attackers.
Code Signing: The process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed.
OWASP Top Ten: A regularly updated report outlining the most critical security risks to web applications, published by the Open Web Application Security Project.
Domain_08: Key Areas
- Understanding and Integrating Security in the Software Development Lifecycle (SDLC)
- Secure SDLC Processes: Adoption of security best practices throughout the stages of software development.
- Security Considerations in Software Acquisition: Assessing and mitigating risks when acquiring software from third parties.
- Security Controls in Development Environments
- Secure Coding Standards and Guidelines: Implementing coding practices that prevent vulnerabilities.
- Code Review and Testing for Security: Techniques for identifying and fixing security issues in code.
- Assessment and Testing of Software Security
- Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST): Tools and methodologies for identifying vulnerabilities in both non-running and running applications.
- Software Composition Analysis (SCA): Identifying risks in third-party components and libraries.
- Secure Deployment and Maintenance
- Deployment Environment and Security: Ensuring secure configuration and management of environments where software is deployed.
- Patch Management and Software Updates: Processes for regularly updating software to address security vulnerabilities.
- Database Security in Software Development
- Protection of Data: Techniques for securing data within applications, including encryption and tokenization.
- Database Security Models and Practices: Applying security controls to databases and ensuring secure database access.
- Cloud, Mobile, and IoT Security Considerations
- Cloud Application Security: Understanding the shared responsibility model and implementing cloud-specific security controls.
- Mobile Application Security: Addressing security challenges unique to mobile platforms.
- Internet of Things (IoT) Security: Considerations for securing IoT devices and the data they generate and process.
- Application Security Frameworks and Standards
- OWASP Guidelines: Leveraging the Open Web Application Security Project (OWASP) resources and tools for web application security.
- Common Security Standards and Frameworks: Familiarity with ISO/IEC standards, NIST guidelines, and other frameworks relevant to software development security.
- Threat Modeling and Risk Management in Software Development
- Identifying and Assessing Software Threats: Methods for predicting and evaluating threats to software.
- Risk Management Strategies: Implementing practices to manage and mitigate risks throughout the software development lifecycle.
Resources
- (ISC)2 CISSP Official Study Guide (OSG) 9th Edition by Mike Chapple, James Michael Stewart, and Darril Gibson
- Chapter 20-21, Pg941-1037
- CISSP All-in-One Exam Guide, Ninth Editionby Fernando Maymi and Shon Harris
- Part VIII, Pg1079-1152
- Eleventh Hour CISSP® Study Guide, Third Editionby Eric Conrad, Seth Misenar, Joshua Feldma
- Domain-08, Pg185-205
- Destination Certification – A Concise Guideby Rob Witcher, John Berti, Lou Hablas, Nick Mitropoulos
- Domain-08, Pg443-476
-
The Official (ISC)2 CISSP CBK Reference, 6th Edition by Arthur Deane and Aaron Kraus
- Domain-08, Pg549-624
Books Reference
Practice Tests
- (ISC)2 CISSP Official Practice Testsby Mike Chapple and David Seidl
- How to Think Like a Manager for the CISSP Examby Luke Ahmed
- Boson Practice Exam
- Study Notes and Theory (SNT) by Luke Ahmed
Videos
- Mike Chapple’sCISSP Cert Prep on LinkedIn Learning.
- Kelly Handerhan’sCISSP Prep Course on Cybrary
- Destination CISSP Mindmap Video
- Pete Zerger’s CISSP Exam Cram
- Prabh’s Coffee Shots
- Luke Ahmed’s Study Notes and Theory (SNT)
Credits & Disclaimer
We express our gratitude to the below-mentioned authors, creators, and sources which have been referred for the creation of our Interactive CISSP Mindmap –Mike Chapple and David Seidl (OSG), Luke Ahmed (SNT), Pete Zerger (Exam Cram), Prashant Mohan (Memory Palace) , Prabh (Coffee shots), Rob Witcher (destcert.com/) and M. Waleed Khaliq (CISSP Concepts Guide).This Mindmap has been meticulously created to ensure that information is shared effectively. This Mindmap aims to offer a thorough grasp of essential concepts with a dedication to assist enhanced learning experiences. We hope that this resource helps people absorb information more thoroughly, which will lead to a broader understanding of each CISSP domains and is freely available for all.
Contribution
We have already included some reference images and short notes for most of the topics so that users can more effectively refer to the content in the mindmap. If you have any information, images, or notes that can make the mindmap more effective, please feel free to share them.
https://github.com/sajinshivdas/CISSP_Interactive_Mindmap/tree/main/CISSP_Domain_08
For issues and concern please feel free to raise a issue in Github link https://github.com/sajinshivdas/CISSP_Interactive_Mindmap/issues
Connect with me www.linkedin.com/in/sajin-shivdas
Related Mindmaps
Find the related mindmaps of CISSP Domains below.