CISM Mindmap-Domain 1: Information Security Governance
An Interactive CISM Mindmap Series
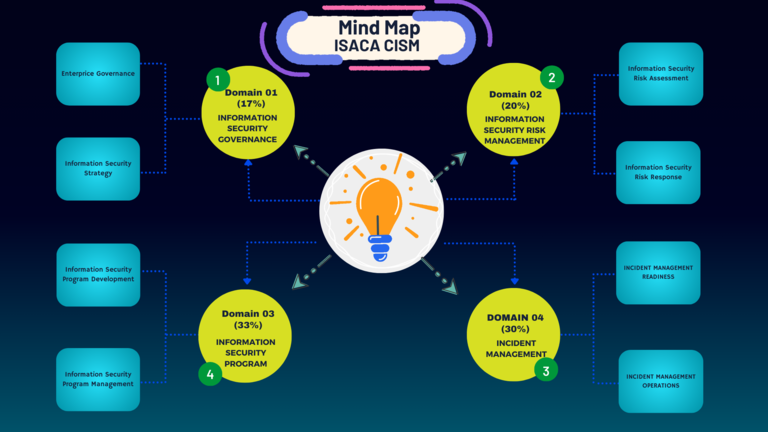
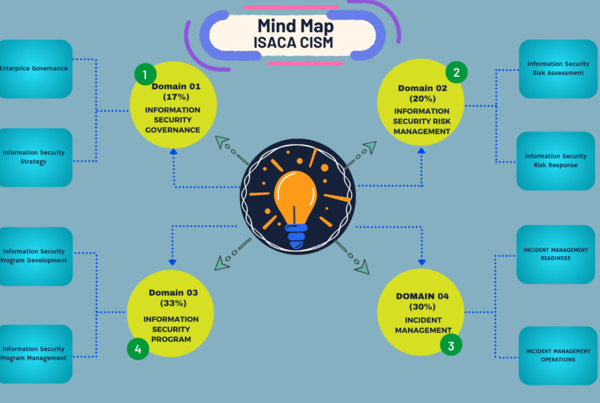
CISM Mindmap – Domain 01
CISM Mindmap Series will include all 4 Domains. This collection is designed to equip prospective CISM aspirants with essential resources for exam preparation, training and reference.
CISM Domain_01: Key Terms & Definitions
- Information Security Governance:The process of establishing and maintaining a framework to provide assurance that information security strategies are aligned with and support the business objectives, while managing risks appropriately and delivering value to the business.
- Strategic Alignment:The practice of ensuring that information security activities are in line with the organization’s objectives and strategic direction, thereby ensuring that security supports business initiatives.
- Security Culture:The set of values, shared by everyone in an organization, that determine how people are expected to think about and approach security. A strong security culture is vital for the effective implementation of a security strategy.
- Third-party Risk Management:The process of analyzing and controlling risks associated with outsourcing to third-party vendors or service providers. This includes managing the security implications of business partnerships and contractual agreements.
- Resource Management:
- The effective and efficient deployment of the organization’s resources, including people, technology, and finances, to manage information security and achieve the objectives set out in the security strategy.
- Performance Measurement:The process of monitoring and assessing the efficiency and effectiveness of the information security program, using metrics and other evaluation tools to ensure objectives are met.
- Value Delivery:Demonstrating the business value of information security investments by optimizing risk management and resource deployment, thus enhancing the organization’s ability to achieve its goals.
- Information Security Strategy:A comprehensive plan that outlines how an organization will implement and manage security measures to protect its information assets and ensure alignment with business goals.
- Governance Framework:The structure of rules, practices, and processes used to direct and control an organization, including the mechanisms to ensure that information security aligns with business objectives.
- Policy, Standards, and Procedures:Documents that collectively define the organization’s security expectations, detail specific security controls, and describe how to implement those controls. Policies provide the overarching principles, standards offer detailed requirements, and procedures outline step-by-step instructions.
- Security Awareness and Training:Programs designed to enhance the security knowledge and behavior of employees, ensuring that they understand the importance of information security, the potential risks, and their responsibilities in protecting organizational assets.
CISM Domain_01: Key Areas
- Establishing and Maintaining an Information Security Governance Framework: Creating a structure that aligns information security strategies with business goals and objectives. This involves defining roles and responsibilities, establishing clear communication channels, and ensuring that information security is integrated into the overall corporate governance.
- Establishing Information Security Strategy: Developing a strategy that supports business objectives and is aligned with the overall risk management approach. This includes understanding business goals, identifying critical assets and information, assessing threats and vulnerabilities, and setting security priorities.
- Alignment of Information Security Strategy with Corporate Governance: Ensuring that the information security strategy complements the broader goals and governance frameworks of the organization. This area focuses on the integration of security practices into business processes, risk management strategies, and corporate compliance efforts.
- Information Security Governance Metrics: Developing and implementing metrics to measure the effectiveness and efficiency of the information security governance framework. This involves selecting key performance indicators (KPIs) that are aligned with business objectives and can demonstrate the value of information security initiatives to stakeholders.
- Establishing Information Security Policies, Standards, and Procedures: Creating the documentation that guides the organization in managing and protecting its information assets. This includes developing policies that set out the organization’s security expectations, standards that detail specific security controls, and procedures that describe how policies and standards are to be implemented.
- Information Risk Management: A critical component of information security governance that involves identifying, evaluating, and managing information security risks. This area focuses on ensuring that risks are identified, assessed, and treated in a manner consistent with business objectives and risk appetite.
- Integration of Risk Management into Business and IT Processes: Embedding information risk management practices into business and IT operations to ensure that risks are identified and managed proactively. This includes the integration of risk assessments into project management processes, IT operations, and business decision-making.
- Security Awareness and Training: Developing and implementing programs to enhance the security awareness of all employees. This includes training staff on security policies, the importance of protecting information assets, and their roles in maintaining security.
Resources
- CISM® Certified Information Security ManagerStudy Guide by Mike Chapple
- CISM Certified Information Security Manager All-in-One Exam Guide, Second Edition, 2nd Editionby Peter H. Gregory
Contribution
We have already included some reference images and short notes for most of the topics so that users can more effectively refer to the content in the mindmap. If you have any information, images, or notes that can make the mindmap more effective, please feel free to share them.
https://github.com/ShivdaSaj/CISM_Interactive_Mindmap
For issues and concern please feel free to raise a issue in Github link https://github.com/ShivdaSaj/CISM_Interactive_Mindmap/issues
Connect with me www.linkedin.com/in/sajin-shivdas