NIST Risk Management Framework (RMF) Mindmap
Risk Management Framework for Systems and Organizations based on NIST Special Publication (SP) 800-37, Revision 2
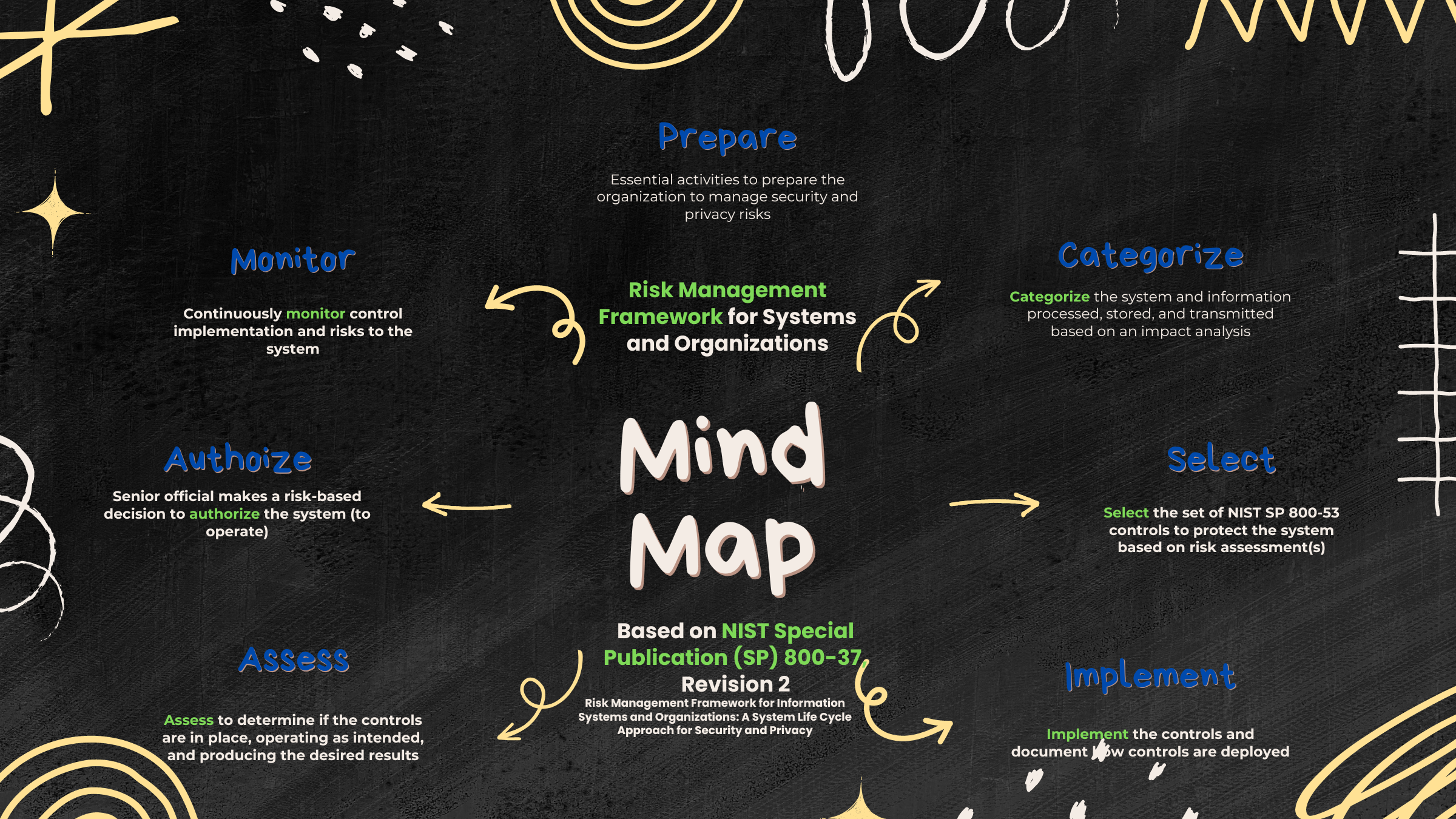
Purpose
Carry out essential activities at all three risk management levels to help prepare the organization to manage its security and privacy risks using the RMF
Organization and Mission/Business Process Level Tasks
P-1: Risk Management Roles|P-2: Risk Management Strategy|P-3: Risk Assessment – Organization|P-4: Organizationally-tailored Control Baselines and CSF Profiles (optional)|P-5: Common Control Identification|P-6: Impact Level Prioritization (optional)|P-7: Continuous Monitoring Strategy – Organization
System Level Tasks (NEW)
P-8: Mission or Business Focus|P-9: System Stakeholders|P-10: Asset Identification|P-11: Authorization Boundary|P-12: Information Types|P-13: Information Life Cycle|P-14: Risk Assessment – System|P-15: Requirements Definition|P-16: Enterprise Architecture|P-17: Requirements Allocation|P-18: System Registration
Purpose
Inform organizational risk management processes and tasks by determining the adverse impact of the loss of confidentiality, integrity, and availability of organizational systems and information to the organization
Tasks
C-1:System Description | C-2:Security Categorization | C-3:Security Categorization Review and Approval (NEW)
Purpose
Select, tailor, and document the controls necessary to protect the system and organization commensurate with risk to organizational operations and assets, individuals, and the Nation.
Tasks
S-1:Control Selection | S-2: Control Tailoring (NEW) | S-3:Control Allocation (REVISED) | S-4:Document Planned Control Implementations (NEW) | S-5:Continuous Monitoring Strategy – System (REVISED) |S-6:Plan Review and Approval
Purpose
Acccomplish the activities necessary to translate the security and privacy controls identified in the system security plan into an effective implementation
Tasks
I-1: Control Implementation | I-2: Update Control Implementation Information (REVISED)
Purpose
Determine if the controls selected for implementation are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security and privacy requirements for the system and organization
Tasks
A-1:Assessor Selection (NEW) | A-2:Assessment Plan | A-3:Control Assessments (MOVED) | A-4:Assessment Reports | A-5:Remediation Actions | A-6:Plan of Action and Milestones (MOVED)
Purpose
Provide accountability by requiring a senior management official to determine if the security and privacy risk to organizational operations and assets, individuals, other organizations, or the Nation of operating a system or the use of common controls, is acceptable
Tasks
R-1:Authorization Package | R-2:Risk Analysis and Determination (REVISED) | R-3:Risk Response (NEW) | R-4:Authorization Decision (NEW) | R-5:Authorization Reporting
Purpose
Maintain an ongoing situational awareness about the security and privacy posture of the system and the organization in support of risk management decisions
Tasks
M-1:System and Environment Changes | M-2:Ongoing Assessments | M-3:Ongoing Risk Response | M-4:Authorization Package Updates | M-5:Security and Privacy Reporting | M-6:Ongoing Authorization | M-7:System Disposal
NIST-Risk Manangement Framework Mindmap
Supporting NIST Publications (RMF steps)
🌍Prepare
- NIST SP 800-30, Guide for Conducting Risk Assessments
- NIST SP 800-39, Managing Information Security Risk: Organization, Mission, and Information System View
- NIST SP 800-53B, Control Baselines and Tailoring Guidance for Federal Information Systems and Organizations
- NIST SP 800-60, Volume 1, Guide for Mapping Types of Information and Information Systems to Security Categories
- NIST SP 800-60, Volume 2, Guide for Mapping Types of Information and Information Systems to Security Categories: Appendices
- NIST SP 800-160, Volume 1, Engineering Trustworthy Secure Systems
- NIST SP 800-161, Supply Chain Risk Management Practices for Federal Information Systems and Organizations
- NIST IR 8062, An Introduction to Privacy Engineering and Risk Management in Federal Systems
- NIST IR 8179, Criticality Analysis Process Model: Prioritizing Systems and Components
🌍Categorize
- FIPS 199, Standards for Security Categorization of Federal Information and Systems
- NIST SP 800-60, Volume 1, Guide for Mapping Types of Information and Information Systems to Security Categories
- NIST SP 800-60, Volume 2, Guide for Mapping Types of Information and Information Systems to Security Categories: Appendices
- NIST SP 800-18, Guide for Developing System Security Plans for Federal Systems
🌍Select
- FIPS 200, Minimum Security Requirements for Federal Information and Systems
- NIST SP 800-53, Security and Privacy Controls for Federal Systems and Organizations
- NIST SP 800-53B, Security and Privacy Controls for Federal Information Systems and Organizations
🌍Implement
- NIST SP 800-128, Guide for Security-Focused Configuration Management of Information Systems
- NIST SP 800-34, Contingency Planning Guide for Federal Information Systems
- NIST SP 800-61, Computer Security Incident Handling Guide
- NIST SP 800-86, Guide to Integrating Forensic Techniques into Incident Response
🌍Assess
- NIST SP 800-53A, Assessing Security and Privacy Controls in Federal Systems and Organizations: Building Effective Security Assessment Plans
- NIST IR 8011, Automation Support for Ongoing Assessment (Multiple Volumes)
🌍Authorize
- no additional NIST publications
🌍Monitor
- NIST SP 800-137, Information Security Continuous Monitoring for Federal Information Systems and Organizations
- NIST SP 800-137A, Assessing Information Security Continuous Monitoring (ISCM) Programs: Developing an ISCM Program Assessment
- NIST SP 800-53A, Assessing Security and Privacy Controls in Federal Systems and Organizations: Building Effective Security Assessment Plans
- NIST IR 8011, Automation Support for Ongoing Assessment (Multiple Volumes)
- NIST IR 8212, ISCMA: An Information Security Continuous Monitoring Program Assessment
(and reference implementation to conduct ISCM Program Assessment)
Disclaimer
This article and the mindmaps are created for quick reference and upskilling your knowledge. Also find the link below to the NIST Portal for the RMF and other Introductory Courses.
